Course Information
Location: Engineering 1044
Meeting Time: T/R 8:10AM - 9:30AM
Office Hours: M 9:00-10:30 & T 9:30-11:00 By Appointment (http://bit.ly/dmb-ohs)
Instructor: Dr. Mike Borowczak
Office: Engineering 4071B
Websites:
Course: http://cs.uwyo.edu/~mborowcz/cosc-4765
CEDAR: http://cs.uwyo.edu/~cedar
Course Objectives and Learning Outcomes
This course explores the foundations of computer security. We will focus on vulnerabilities and attacks that exploit them from buffer overflows, SQL injection, and session hijacking to targeted malicious software. We will study attacks in order to learn how to create defenses that can prevent and mitigate these attacks. This course will consist of traditional lectures, flipped classroom activities, research surveys, mini-projects (homework), a final culminating project and exam.
Course Topics
- Ethics and Security
- Practical Security
- Physical Security & Disaster Recovery
- Information & Digital Security
- Cryptography
- Application & OS Level Security
- Network Security
- Viruses, Worms, Malware, and Trojans
Required Texts and Materials
While there is no required text for this course, we’ll be using quite a bit from Security Engineering (2nd Edition) by Ross Anderson. The book is available for free online https://www.cl.cam.ac.uk/ rja14/book.html and in printed hardback form. Another book that covers some fundamentals is Security in Computing (5th Edition) by Pfleeger, Pfleeger and Margulies. If you find a different book that you like, whether that’s during the course or years from now - please let me know and I’ll include it on the course site.
Computer Security is a constantly evolving field, we’ll also use current and seminal papers, forum posts, documents and other work to ground our discussion - you’ll be expected to complete the assigned reading prior to class, otherwise our discussions will be rather one-sided. Computer security is about details - if I make a mistake, or if you have a question - ask - let’s get on the same page. I won’t have all the answers to all of your questions - in those scenarios - you can either 1) wait for me to find the answer or 2) find the answer and build up our community of knowledge. We’ll use Piazza for collaboration and discussions on class topics, homework, and projects. Our Piazza course site is: http://piazza.com/uwyo/spring2017/cosc4765.
COSC 4765 requires the use of a computer, preferably your own, with a virtual machine (VM) player e.g VM Ware player (Windows/Mac) or KVM (Linux). The CS computer labs should have the needed virtual machine software, but it may be impractical to download/save VM images to those accounts - consider investing in a larger USB external drive to store your VM images.
Assessments
- Participation & Attendance (100 points)
- Your attendance and participation in class will be measured through informal assessments; -4pt per absence after the 2nd ”unexcused” absence.
- Writing Assignments (100 points - 4 @ 25 pts each)
- including an ethics paper and three research summaries. A template for the research summaries will be provided (LATEX and MS Word) and is required. The summaries will be aggregated and posted on the course and CEDAR website.
- Homework Projects (300 points - 5 @ 60 pts each)
- Real world tools and attacks. These are time consuming. Plan accordingly.
- Final Project & Presentation (400 points)
- A group project covering a demo of a complete attack or exploit (fully sandboxed), an analysis of a novel exploit or attack, and/or a cyber-security related educational outreach activity. Other ideas welcomed.
- Final Exam (100 points)
- All inclusive, covering material from lecture, the homework-projects, and the final projects.
Grade Policies
Your grade will be computed as a direct unweighted sum of the all the in-class participation, homework, mini-projects, final project, final presentation, and exam scores. The following point boundaries will be used to determine final grades.
| Points | Letter Grade |
| >899 | A |
| 800-899 | B |
| 700-799 | C |
| 600-699 | D |
| <600 | F |
If necessary, all or any results will be curved. The curve will only ever be upwards (i.e., only ever in your favor). Average numerical grades will be rounded to the nearest whole number (that is, 799.5 becomes 800 and a B, 799.4 becomes 799 and a B). I may relax these grade boundaries but only ever in you favor (i.e., it might be possible that the A grade boundary ends up being 880 instead of 899.0...).
A summary of your grades will be posted on UW’s WyoCourses site. Please review your scores and report any discrepancies to me.
Late Work
Late work will only be accepted for credit 24 hours after the assignment due date . You will receive a
maximum of 75% of the earned points for late work submitted within 24 hours of the due
date. E.g. if an assignment is worth 25 points, is submitted 22 hours after the due date, and
would have received 20 points if submitted on time, the late-score would be computed as
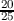 ×
×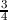 =
= 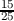
Late work that is submitted after the due date and prior to exam will remain ungraded until the end of the semester. At the end of the semester - the late work will only be graded, at the sole discretion of the instructor, if it affects the pass/failure of the course. The maximum course grade you can receive in this scenario is a C. Late work will not be accepted after the final exam.
Miscellanea: Extra Credit, and Expectations
No separate extra credit assignments will not be offered or made available. Rather, assignments and projects may contain an opportunity to gain extra credit.
Attendance/Participation Policies
It is expected that you attend class regularly, and your grade will be affected positively if you are present in class. As an active and engaged learner, you are expected to attend and arrive punctually to our scheduled classes. engagement throughout the class is critical to your ultimate learning. Your participation and attendance will contribute to 10% of your overall score.
- University-sponsored absences are cleared through the Office of Student Life;
- Student Health or your private physician may issue a statement giving the dates of students confinement whether in the home or hospital due to illness;
- Roads & Weather: if you regularly travel from outside of Laramie, please let me know now. If the University remains open, and the road conditions prevent you from attending physically, we can set up some web-based video-call given sufficient notice;
- If you have a conflict (expected or not), please let me know as soon as possible;
- After the second ”unexcused” absence, -4pt / class.
Academic Honesty
The University of Wyoming is built upon a strong foundation of integrity, respect and trust. All members of the university community have a responsibility to be honest and the right to expect honesty from others. Any form of academic dishonesty is unacceptable to our community and will not be tolerated. Teachers and students should report suspected violations of standards of academic honesty to the instructor, department head, or dean.
Any and all suspicions of academic dishonesty shall be investigated in accordance with UW Regulation 6-802 (http://www.uwyo.edu/generalcounsel/_files/docs/uw-reg-6-802.pdf). Evidence of academic dishonesty will result in one or more of the recommended sanction, in accordance with UW Regulation 6-802 6.A.
Academic Civility
”There are several misconceptions about intellectual diversity and academic freedom... ...the narrower
concept of academic freedom does not mean the freedom to say anything that one wants. For example,
freedom of speech does not mean that one can say something that causes physical danger to others. In a
learning context, one must both respect those who disagree with one and also maintain an atmosphere of
civility. Anything less creates a hostile environment that limits intellectual diversity and, therefore, the
quality of learning.”
Association of American Colleges and Universities
Board of Directors Statement on Academic Freedom and Responsibility 12/21/05
Disability Support Services
If you have a physical, learning, sensory or psychological disability and require accommodations, please let me know as soon as possible. You will need to register with, and possibly provide documentation of your disability to University Disability Support Services (UDSS) in SEO, room 109 Knight Hall. You may also contact UDSS at (307) 766-6189 or udss@uwyo.edu. Visit their website for more information: www.uwyo.edu/udss.
Expectations
Student’s Role & Expectations
You are expected to treat all members of the class and your instructor with respect. Plan to attend class, take an active part in discussion or teamwork, and complete all readings and assignments by the deadlines listed in the syllabus.
Professor’s Role & Expectations
I will follow a professional code of behavior and responsibility. I will treat all members of the class with respect. I will attend class and take an active part in your learning. In each class I will ask: 1) What do I want you - my students - to learn? 2) How will you learn it? 3) What do I want you to do with the information? and 4) How will I assess your learning?
Warning
In this course, you’ll learn and implement attacks on computer systems with the objective of understanding how to design defenses. Do not attack any system or information without explicit prior (written) permission. Not only is it a really bad idea, it probably illegal and/or at a minimum a violation of UWYO network rules (UW Regulation 3-690) http://uwyo.edu/generalcounsel/_files/docs/uw\%20reg\%20updates\%202015/uw\%20reg\%203-690.pdf, and the CEAS technology policy: http://uwyo.edu/ceas/resources/current-students/techpolicy.html. Please don’t do it! Most of our work will be contained within local, virtual machine sandboxes, you should not carry out any the attacks covered across any network. When in doubt - ask.
Syllabus Change Policy
This syllabus is only a guide for the course and is subject to change with advanced notice.1
Course Schedule
28 scheduled meetings, including 4-5 flex topics of your choice (and/or a buffer). The course breaks down into roughly 2-3 week overarching topic including: the fundamentals of data and information, security 101, OS security, application security, and network security.
|
Monday |
Tuesday |
Wednesday |
Thursday |
Friday |
Saturday |
|
Jan 23rd
|
24th 1
Overview, Ethics, Threat Models
|
25th
|
26th 2
Hijacking Attacks
|
27th
|
28th
|
|
30th
|
31st 3
Buffer Overflow
|
Feb 1st
|
2nd 4
Privilege Separation
|
3rd
|
4th
HW #1 Due
|
|
6th
|
7th 5
Capabilities
|
8th
|
9th 6
Sandboxing
|
10th
|
11th
|
|
13th
Ethics Paper Due
|
14th 7
Web security
|
15th
|
16th 8
Securing Web Apps
|
17th
|
18th
|
|
20th
Project Proposal Due
|
21st 9
Symbolic Execution
|
22nd
|
23rd 10
Web
|
24th
|
25th
HW #2 Due
|
|
27th
|
28th 11
Network Security
|
Mar 1st
|
2nd 12
Network Protocols
|
3rd
|
4th
|
|
6th
Rsrch Summary #1 Due
|
7th
Project Work Day
|
8th
|
9th
Project Work Da
|
10th
|
11th
HW #3 Due
|
|
13th
|
14th
No Class Spring Break
|
15th
|
16th
No Class Spring Break
|
17th
|
18th
|
|
20th
Intermediate Report Due
|
21st 13
SSL / HTTPS
|
22nd
|
23rd 14
Medical Software
|
24th
|
25th
|
|
27th
Rsrch Summary #2 Due
|
28th 15
Side Channel Attacks
|
29th
|
30th 16
User Authentication
|
31st
|
Apr 1st
HW #4 Due
|
|
3rd
|
4th 17
Private Browsing
|
5th
|
6th 18
Anon. Communication
|
7th
|
8th
|
|
10th
Rsrch Summary #3 Due
|
11th 19
Wireless Attacks
|
12th
|
13th 20
Mobile Phone Security
|
14th
|
15th
|
|
17th
|
18th 21
Data Tracking
|
19th
|
20th 22
Malware Randsomware
|
21st
|
22nd
HW #5 Due
|
|
24th
|
25th 23
Economics of Attack
|
26th
|
27th 24
Flex Topic
|
28th
|
29th
Research Report Due
|
|
May 1st
Poster Outline Due
|
2nd 25
Flex Topic
|
3rd
|
4th 26
Flex Topic
|
5th
|
6th
|
|
8th
Final Exam Week
|
9th
|
10th
|
11th
|
12th
|
13th
|
|
|
|||||
|
|
|||||
|
|
Homework - Mini Projects
Each assignment will include a specific grading rubric. Generally, you will be expected to turn in:
- your own homework solutions (using any provided LATEXor Word templates),
- any code used in generating your answers (code, dependencies, Makefiles as needed),
- a list of collaborators.
The preference for code submissions is a link to a public git/cvs/svn repository. Code check-in’s and updates are a great way to show ownership over time. Alternately, provide a zip file with all code, dependencies, and a makefile.Homework is due no later then 2PM (Mountain) on the given due date (generally Saturday).
While the current planned set of mini-homeworks is show below, this list may get modified based on the trajectory of the course.
- L1 - Kali Linux, PGP, and JTR
- L2 - Buffer Overflow
- L3 - Privilege Escalation
- L4 - WiFi Security
- L5 - Browser Security
Writing Assignments
Each writing assignment will include a specific grading rubric. Generally, you will be expected to:
- ”Sign up” for an exploit topic online,
- use any template (if provided),
- include a list of references (in any consistent format).
Writing assignments are due no later then 11:59PM (Mountain) on the given due date (generally Monday).
The current planned set of writing assignments includes the following:
- P1 - Ethics Paper
- S1 - User Exploit
- S2 - Software Exploit
- S3 - Your Choice of Exploit
Research Project
Objective: Exploit, protect, and/or demonstrate a current/relevant vulnerability to our cyber-infrastructure.
Overview
This course will provide you with an overview of Computer Security fundamentals, but in order to truly understand the nuances and complexity of Computer Security, you have to experience the challenge of protection and attack for yourself. This project enables you to have a real-world experience that you bring to an interview, your own research, or some personal project. As with any real-world endeavor, you must be able to effectively communicate your work to your peers (experts and non-experts alike).
You will work in teams of 3 or 4 (teams of n < 3 or n > 4 are highly discouraged barring and special needs or requirements). If you have a case for teams sizes not equal to 3 or 4 please come talk to me.
Deadlines
All project components, except for the poster presentation, are due no later then 11:59PM (Mountain) on the given due date (generally a Monday). The poster presentation will be held during our final day of class. In the event of a weather calamity day, the exam period will be split to accommodate the poster presentations. Project guidelines and scoring rubric will be provided no later than February 4th.
-
Proposal
(25pts)
Due February 20th -
Mid-term
Report
(75pts)
Due March 20th -
Final
Report
(250pts)
Due April 29th -
Poster
Outline
&
Poster
(30pts)
Due May 1st -
Poster
Presentation
(70pts)
Due May 4th